这几天在网上找了一些视频百度网盘资源,找着找着发现已经整理很多分享链接了,由于自己比较懒不想一个个打开链接转存,就尝试写个脚本自动将所有资源转存到自己的网盘,在这里记录一下过程。
随便打开一个百度网盘分享链接,输入链接提取码,点击保存到网盘,可以抓取到下面数据:
接口:https://pan.baidu.com/share/transferquery:
{
"shareid": 2411602035,
"from": 1101662586930,
"sekey": "4N4PdSB7q4mO7deAokdDdf3VC5fjGpPIHW8ousaLXMc=",
"ondup": "newcopy",
"async": 1,
"channel": "chunlei",
"web": 1,
"app_id": 250528,
"bdstoken": "1ed1cd98bd64d1e1410406c0c8abe75d",
"logid": "MDgzRTMzN0VGQzdDNUE3NzNFQzE1NkVCOEUxMDc5ODQ6Rkc9MQ==",
"clienttype": 0,
"dp-logid": 45577800245178080034
}formData:
{
"fsidlist": [1008563889679426],
"path": "/"
}清除Cookie,开始分析请求过程。
刷新一下页面,发现链接会重定向到输入提取码的页面。输入提取码后,页面跳转到分享内容,页面链接也变成了分享链接。再次刷新页面,这时不会再跳转到输入提取码的页面,由此猜测在输入提取码后返回协议头中存了Cookie,带着这个Cookie请求分享链接时,不会跳转到输入提取码的页面。
重新清除Cookie刷新页面并输入提取码进行抓包,可以发现下面信息:
接口: https://pan.baidu.com/share/verifyquery:
{
"t": 1657161792654,
"surl": "c8Nt90SMxV_Pm0pP3eJKjg",
"channel": "chunlei",
"web": 1,
"app_id": 250528,
"bdstoken": "",
"logid": "QTREQTU5NjFBNzc0MUIwQzA2NkVFNDdFQzgwQjRFRkY6Rkc9MQ==",
"clienttype": 0,
"dp-logid": 68359100918157540014
}formData:
{
"pwd": "qz1g",
"vcode": "",
"vcode_str": ""
}一个一个分析参数:
t:猜测是时间戳
surl:没有在接口中看到,找了一会发现在分享链接重定向的地址中,也就是输入提取码地址的query部分:https://pan.baidu.com/share/init?surl=c8Nt90SMxV_Pm0pP3eJKjg
channel:上面接口也用到这个参数,猜测写死为chunlei
web:猜测写死为1
app_id:同上面接口也用到这个参数,猜测写死为250528
bdstoken:为空
logid:这个参数找了很久,在接口、页面源码、Cookie中都没有找到,猜测是js加密后的数据,便在页面的js中搜索这个字符串,发现在https://nd-static.bdstatic.com/m-static/disk-share/js/boot_e3992d7.js这个js中,向前查找这个参数的机密规则,可以找到这段代码:
n = t.tools.baseService.base64Encode(a.getCookie("BAIDUID"));
由此可见logid是一个base64编码,被编码的值是Cookie中的BAIDUID
clienttype:猜测写死为0
dp-logid:同logid查找思路,最后在https://staticiot.cdn.bcebos.com/union/bpdatajs-sdk-min-1.3.3.js中找到该值的生成函数,但是这个函数里面用到了很多变量,一个个找感觉很麻烦,用postman尝试一下删除该字段并发送请求,发现居然成功了,猜测该字段作用不大,就不作添加了
最后剩下formData中有个很明显的提取码pwd字段,所有输入提取码接口用到的参数都获取到了,调用这个接口后,在返回的协议头中可以发现存了BDCLND这个Cookie。
带着这个Cookie请求分享链接,就可以直接进入分享文件列表页面了,下面分析转存的接口参数:
shareid:在所有的Fetch/XHR请求返回值没有找到该字段,便尝试在在网页源码中搜索,发现在分享链接里面源码中存了一大段json数据:
{
"csrf": "xxxx",
"uk": "xxxxx",
"username": "xxxxx",
"loginstate": 1,
"vip_level": 1,
"skinName": "white",
"bdstoken": "xxxxxx",
"photo": "https://dgss0.bdstatic.com/6LZ1dD3d1sgCo2Kml5_Y_D3/sys/portrait/item/09cee890bde88ab1e5b08fe5b08fe58fb63f4f",
"is_vip": 0,
"is_svip": 0,
"is_evip": 0,
"now": "2022-07-07T02:24:18.104Z",
"XDUSS": "xxxxx",
"curr_activity_code": 0,
"show_vip_ad": 0,
"share_photo": "https://himg.bdimg.com/sys/portrait/item/public.1.dae0c21c.h14g_oxl4r_LOvAXtBWRmg.jpg",
"share_uk": "1101662586930",
"shareid": 2411602035,
"hit_ogc": false,
"expiredType": 0,
"public": 0,
"ctime": 1618227936,
"description": "",
"followFlag": 0,
"access_list_flag": true,
"Elink_info": {
"isElink": 0,
"eflag_disable": false
},
"owner_vip_level": 1,
"owner_vip_type": 2,
"linkusername": "gon****gre",
"share_page_type": "multi",
"title_img": ["iVBORw0KGgoAAAANSUhEUgAAARsAAAAeCAIAAACT9S1xAAAFLUlEQVR42uzcbWhS7xsH8HvOttYTbgSz4sRoPcAq1kaMFUFP1GFjLBjZIhuMLVr0okH0ALNiVh59kUFFCWHkyYgghSA1iSQ1xUoli0RTsXwATWFkhmlnev7QiZPUv4cf9KbD9Xl17mvXzoHdfnfu3TeMT9M0AgD8JTz4EQAAiQIAEgUAJAoAAIkCABIFACQKAPCrRFmt1tu3b//XW1AUNTw8nMvlft1msVhu3LjBDo1GY7FYhAkAXE7U5OTkhw8fEEITExPCH2g0GqaNpunpKp8/fyZJ8uPHj9XFHw+O3W63yWRirsvl8rVr1zo7O30+H8wB4JIa9qPvcDj27dv36tUrPp/PpKK6b+/evTt37ty9ezdCyGw29/b21tXVsV8tlUr19fXVw8ePH2/YsCEUCjERRQiRJBkKhWQyGdtmMBh0Op3P5+Pz+TATgBu+fZQlEglBEC6XSy6XHz16VKlUVvc9e/Zs//797HD58uXBYJC5LhaLDQ0Nb9++FQqFTKWhoYG5vnDhwtOnT5liOp0uFAoHDhxghoFAgCTJiYkJiBPgYKJu3brF4/EGBgbWr1+/Z8+e9vb2ycnJ6j6xWNzU1PQnd5yamioWi0yiLl++zNYVCoXP52P/TmtraxMIBNUvOgC4kyiTyeT1eufOndva2rpx48aLFy9+15fNZjUajcfjYV4y09PTyWSSXeMhhFKpFLNQpGk6Ho/PmTPnt8H7w4gC8O8liiTJUqnU1tZ25cqVWbNmNTU18Xg8hJDf73/48OH4+Pjp06cRQo2NjUx/PB7v7u7OZDKLFy9GCLW2topEIiZO0WjUZrNhGOb3+xOJBPukUCiUTqfNZjMzfP/+/YsXL7LZLI7jMA2AgzsThw4doihKpVIhhHp6egYHB4eHhw0Gw8jISDKZrFQqYrH4xIkTHR0dd+/elUqlDoejpaXFarWuXLmSvd3169cJgvD7/XV1defPn2c39xBCsVgsn8+vWrWKrXz69Mnr9cIeOuAU+guz2czj8cbGxvr7+y9duvTmzRsMwywWy7179xBCBEFs2bJFLBZTFEXTtFqt3rx5M03TSqVy3bp1TJGm6UgkIhAIHjx4QP8/crl8cHCwuhIOh+fNm0cDwCHfzqOGhoaWLFkyOjoqEolaWlqcTqfdbn/+/PmKFSsIgli2bJlWq2X25aLRKLPYGx8fr6+vHx0dLZfLyWQSx/GDBw9u27btD8NcKpVmzpwJv9QAl3xNFI7jGo3m2LFjOI7PmDHD6XT29fW53e758+cLhcJz5849evQoHo8zzW63e82aNQih2tpavV4fCAS2bt3a1dXV19dXfdz0M7FYLJfLVSqV+/fvYxgGcwA4mCi73S6RSDZt2sTkp7+//8iRI0ajcdGiRTU1NWNjYyKRqKOjQ6vVZjIZm83W09PDfOPr16+bm5s9Hk8mk6Eo6uXLl799pEKhEAgEtbW1Z86cOXnyJMwB4GCiXC5XuVw+depUKpUiCCISiVQqlZs3b169enXhwoUIobNnz6rV6q6uLplM1t3dXSgUpFLp6tWre3t729vbE4nEkydP3r1719nZuXTp0pGREb1e/7NHqlSqfD4/9cWOHTtgDgCXfN09P378eHW1sbExGAyGw+EFCxZIJBKmODAwgBDavn370NCQw+Gw2WyHDx/etWvX7NmzEUJr167V6XTpdPrOnTtGo7G5ufm7J2EYxm7r/fa0CoB/VA38LyQA/v6qDwAAiQIAEgUAJAoAAIkCABIFACQKAMD6XwAAAP//RtZFtMQ2mowAAAAASUVORK5CYII="],
"file_list": [{
"app_id": "250528",
"category": 6,
"delete_fs_id": "0",
"extent_int3": "1101662586930",
"extent_tinyint1": "0",
"extent_tinyint2": "0",
"extent_tinyint3": "0",
"extent_tinyint4": "0",
"file_key": "",
"fs_id": 1008563889679426,
"isdelete": "0",
"isdir": 1,
"local_ctime": 1567180308,
"local_mtime": 1567180308,
"md5": "",
"oper_id": "1101662586930",
"owner_id": "0",
"owner_type": "0",
"parent_path": "%2Fsharelink1101662586930-1008563889679426",
"path": "/sharelink1101662586930-1008563889679426/绿皮书",
"path_md5": "7543596033052499211",
"privacy": "0",
"real_category": "0",
"root_ns": 5132615750,
"server_atime": "0",
"server_ctime": 1567180308,
"server_filename": "绿皮书",
"server_mtime": 1618227928,
"share": "0",
"size": 0,
"status": "0",
"tkbind_id": "0",
"videotag": "0",
"wpfile": "0"
}],
"errortype": -1,
"errno": 0,
"ufcTime": 771,
"self": 0,
"elink_self": 0
}在这段json中找到了这个参数值,还可以找到from(对应字段为share_uk)、bdstoken字段
sekey:为Cookie中的BDCLND值
ondup:猜测写死为newcopy
async:猜测写死为1
channel:猜测写死为chunlei
web:猜测写死为1
app_id:猜测写死为250528
logid:同上面提取码验证接口获取方式
clienttype:猜测写死为0
dp-logid:同上面提取码验证接口不加
formData中的fsidlist字段值可以取上面网页源码一大段json中的['file_list'][0]['fs_id'],path为保存的目录,/为根目录
最后,将上面两个用到的接口封装好,循环调用就可以转存了,测试一下效果:
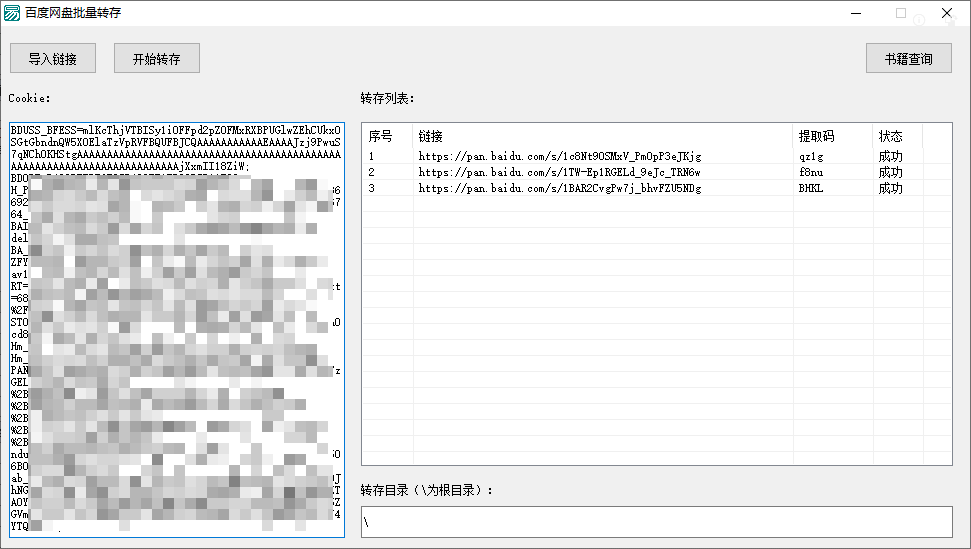

34 条评论
大佬,请问一下,我抓包进行分析,没有PWD这个参数了,而且也不知道提取码在啥时候提交的
每一个段落都紧密相连,逻辑清晰,展现了作者高超的写作技巧。
文化符号解读精准,展现独特审美。
哈哈哈,写的太好了https://www.lawjida.com/
《倒霉性爱,发狂黄片》喜剧片高清在线免费观看:https://www.jgz518.com/xingkong/63886.html
《007之生死关头》动作片高清在线免费观看:https://www.jgz518.com/xingkong/46324.html
《怪兽猎人》剧情片高清在线免费观看:https://www.jgz518.com/xingkong/74083.html
《倒霉性爱,发狂黄片》喜剧片高清在线免费观看:https://www.jgz518.com/xingkong/63886.html
你的文章让我感受到了正能量,非常棒! http://www.55baobei.com/aekwv9r4qe.html
你的才华让人瞩目,期待你的更多文章。 http://www.55baobei.com/5ITpShxfOg.html
你的文章充满了创意,真是让人惊喜。 http://www.55baobei.com/OnqeFlsHnS.html
《IQ笨蛋国语》喜剧片高清在线免费观看:https://www.jgz518.com/xingkong/24315.html
《熊出没之夺宝熊兵》喜剧片高清在线免费观看:https://www.jgz518.com/xingkong/16273.html
真好呢
《娘道网络版》国产剧高清在线免费观看:https://www.jgz518.com/xingkong/148494.html
《可爱的中国》剧情片高清在线免费观看:https://www.jgz518.com/xingkong/66841.html
你的文章内容非常卖力,让人点赞。http://www.huamulanchina.com
不错不错,我喜欢看 https://www.237fa.com/
怎么收藏这篇文章?
想想你的文章写的特别好https://www.jiwenlaw.com/
zeoawb70218GI-8个良心网贷平台http://www.slearning.cn/tags-69014.html/
这篇文章写得深入浅出,让我这个小白也看懂了!
你好,看完你的博客文章,感觉很不错!希望与你网站首页友情链接
流量卡知识网
http://53go.cn/
专注于移动/联通/电信推出的大流量多语音活动长短期套餐手机卡的相关知识的介绍普及
听说互换友情链接可以增加网站的收录量,特此来换,如果同意的话就给internetyewu@163.com[微信ganenboy]发信息或者就在此回复下吧!【建站问题也可以一起讨论!】
获取cookie:随便打开一个分享链接,不要输入密码,复制第一个请求的cookie,按这个搞了几次都报错。。貌似这个
{"errno":200025,"newno":"","request_id":1373630002402447166,"show_msg":"提取码错误"}
1
我也是这个错误
可以试一下楼下说的传所有id,源码里面只传了第一个
OK了,感谢大佬无私奉献。。。
返回的['file_list']是个list,不要只拿第一个的id,全都要!
应该是的,可能我保存的都只有一个根目录没有报错
可以分享下源码吗,谢谢大佬
我这边重现出来了
可以分享下源码吗,谢谢大佬
链接:https://pan.baidu.com/s/10zOy4Jd76HF-N-n1z_6EWQ
提取码:s24d
刚整理完,如果出问题的话可以参考一下 https://bwmelon.com/archives/45/#comment-265 传入所有文件